Security
More secure than any cloud.
Risks in Cloud Based Training
vs.
→ You have to transfer all your data to one or more instances
→ You need you to secure each instance
→ You need to worry about security of both your data and your model during the DevOps process
Security Benefits of Swarm based Training
→ Your data and model stay in our private environment
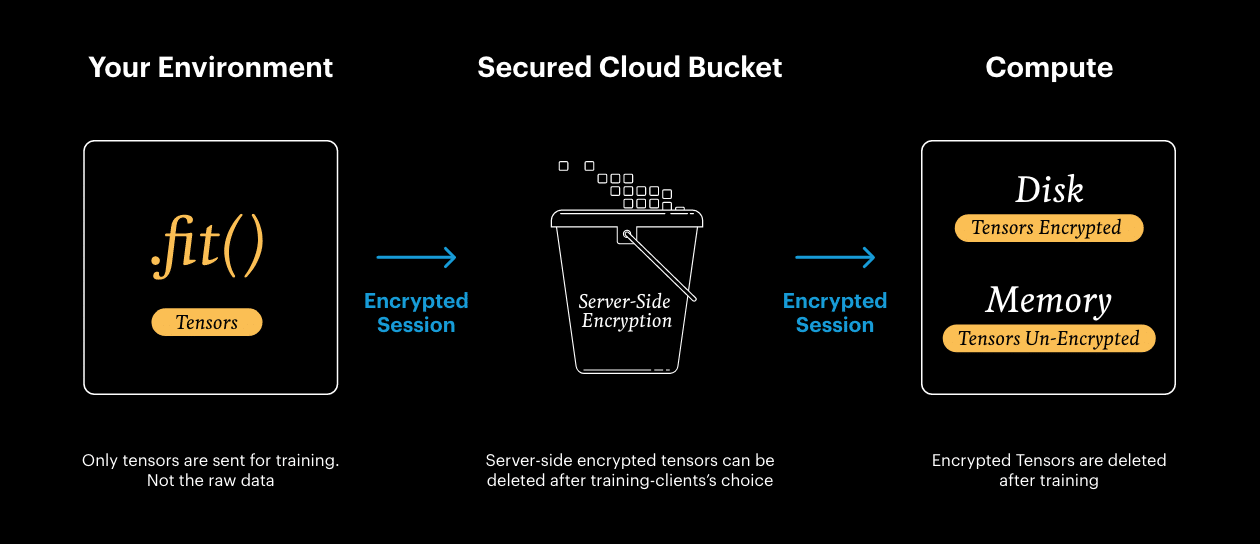
→ Only tensors are sent for training
→ All data is encrypted during transit and when at rest
SwarmOne developed an “instance-less” technology, that runs on swarms of GPUs. It enables companies to run AI model training, dynamically and seamlessly, without ever caring about Cloud instances in public Clouds.
Security at SwarmOne
Security at SwarmOne
Our Commitment to Security
At SwarmOne, we prioritize the security of our systems and the protection of your data. We understand the importance of trust in our technology and services. Our dedicated security team is committed to providing a secure and reliable environment for all our users and customers.
Secure by design
SwarmOne allows you to work from your own environment, you work on your training code, and all the engineering is abstracted away, we seamlessly handle the technical complexities – and the security.
There’s no need for you to worry about mounting buckets, granting permissions, or opening ports—it’s all magic, taken care of for you.
Application Security
● Software dependencies are audited by Github’s Dependabot.
● We use HTTPS for secure connections. HTTPS is forced for all services using TLS (SSL), including our public website, Dashboard and APIs to ensure secure connections.
● All public SwarmOne APIs use TLS 1.3, the latest and safest version of the TLS protocol.
● Internal code reviews are performed using a modern, PR-based development workflow (Github), and engage external penetration testing firms to assess our software security.
● We have automated synthetic monitoring test applications that continuously check for network and application isolation within our runtime.
● All data transmitted to and from SwarmOne is encrypted using industry-standard protocols. We ensure that sensitive data stored in our databases is encrypted at rest, safeguarding your information from unauthorized access.
Corporate Security
All SwarmOne employees have secure access to the company infrastructure.
● Access to our services and applications is gated on a SSO Identity Provider (IdP).
● We mandate phishing-resistant multi-factor authentication (MFA) in all enrolled IdP accounts.
● We regularly audit access to internal systems.
Infrastructure Security
SwarmOne ensuring a hardened, minimal attack surface for components we deploy on our network.
● SwarmOne implements strict network monitoring and protection with firewalls, IDS, and IPS to secure against unauthorized access and attacks.
● We enforces access control with RBAC to restrict network and data access based on user roles, ensuring access is job-specific.
● SwarmOne uses logging and metrics observability providers, including Datadog and Sentry.io.
● We conduct annual business continuity and security incident exercises.
Continuous Improvement and Vulnerability Remediation
Security at SwarmOne is an ongoing effort. We continuously monitor our systems for vulnerabilities and apply updates and patches promptly. Our security team stays abreast of the latest security research and trends to enhance our defenses.
SOC 2 Certified
SwarmOne is also SOC2 Type 2 certified, meaning we provide security certification to our customers and actively monitor and patch any security weaknesses.
Questions?
For any security concerns or inquiries, please contact our security team at security@swarmone.ai. Your privacy and security are of utmost importance to us, and we are here to address any questions or concerns you may have.